-
After years of cyber criminals silently pressuring businesses to pay up, data breach reporting is back on the rise. But this time with a new sting in the tail.
In a typical ransomware incident, attackers encrypt the data on all systems of a target’s network and demand payment of large sums of money for the decryption key. This model relies on pressuring business leaders into silently paying their way out of trouble.
“Ransomware actors who aren’t detected quickly are just as likely to steal a target’s data and threaten executives with disclosing it if they aren’t paid.”
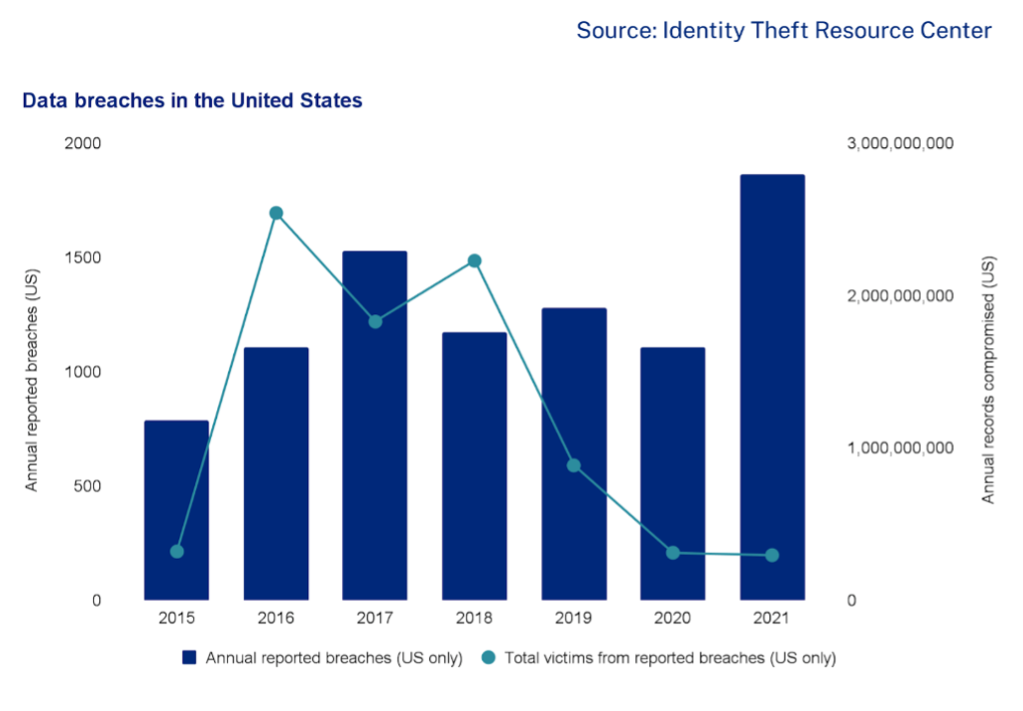
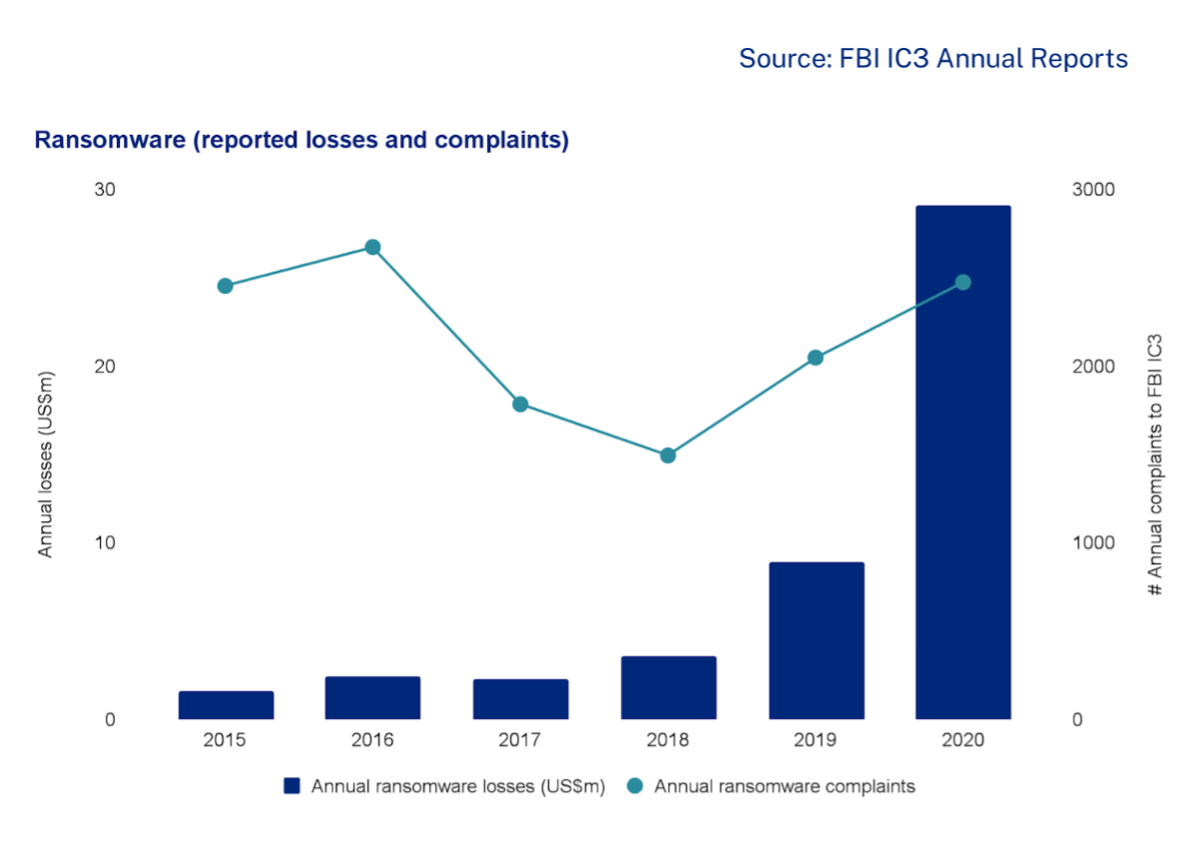
So paradoxically, while payments made to ransomware actors have exploded since 2017, there was a corresponding decline in the total number of reported data breaches as a significant number of organisations weren’t reporting breach events at all. As a result, several proposed laws in Australia, the United States and other countries aim to compel company directors to report them to regulators.
{CF_IMAGE}
In 2021, the trend was reversed. For the first time in four years, there were a larger number of reported data breaches observed by the Identity Theft Resource Center (ITRC).
Why? Because ransomware actors who aren’t detected quickly are just as likely to steal a target’s data and threaten executives with disclosing it if they aren’t paid.Double extortion
A double extortion event refers to ransomware attacks in which a target’s data is pilfered from the network before the organisation’s systems are rendered inaccessible.
This technique was developed to motivate company directors to pay a ransom, even when the option of restoring systems from backup was available. When extortion negotiations aren’t proceeding smoothly, the attacker publishes a salacious tidbit of the stolen data on a “leak site” on the dark web with the promise the entire volume of stolen data will be published if the ransom isn’t paid.
Ransomware gangs routinely make journalists aware of these leak sites.
{CF_IMAGE}
It’s a way of making sure company directors feel the maximum amount of pain and pressure to pay up. It anticipates every organisation stores information they would be strongly motivated to keep confidential. Attackers want decision makers to swiftly come to the conclusion the quickest and safest way out of trouble is to simply pay up.
A variation on double extortion is when lower-skilled ransomware affiliates (attackers who “lease” ransomware infrastructure for a cut of the profits) are only able to gain limited access to a target’s data and steal what they can prior to detection or eviction from the network.
These attackers grab what data they can access from the beachhead where they land or the one or two accounts they control and extort their victims over threats to release that limited set of data. These lower-skilled actors are less likely to get paid and company directors are more likely to report the incident – given they can demonstrate success in preventing a broader compromise.
{CF_IMAGE}
In this environment, the likelihood of a ransomware encounter in any medium or large organisation is far greater. An organisation’s defensive strategy must anticipate these events and limit what a single compromise can yield to the attacker.
That requires both limiting the amount of data accessible from any given device or account and investing in ways to detect and respond faster.
A zero-trust approach
According to the ITRC, the current threat environment warrants a “zero-trust” approach to security. That is to always verify access to a system or to data.
Zero-trust is about getting back to information security basics. It recognises it is no longer sufficient to decide whether a device or user is trustworthy exclusively on whether it has previously authenticated to an internal network.
It also recognises modern approaches to identity and access management can enforce the “principle of least privilege” without imposing additional friction on users.
Users and devices must instead authenticate every time they access applications and data and every authentication should assess a broader set of contextual information about the request. This should include user context (such as the relative strength of the authenticator used to prove their identity), device context (whether the device is known/registered, managed, and demonstrating a strong posture) and network context (whether the request came from a known and reputable network location/IP type).
These assessments should also take behaviour into account: is a user identity typically associated with this device and network?
The primary enablers for zero-trust is a policy engine that can assess this context, controls (like multifactor authentication) used to challenge users to prove their identity and an ability to easily log, monitor and respond to events indicative of account compromise.
Are we there yet?
According to Okta’s zero-tust report, business leaders in Australia and New Zealand are aware of the threat posed by ransomware and are actively investing in the technology and processes required to mitigate it.
The research revealed 85 per cent of organisations in Australia and New Zealand plan to implement some form of zero-trust in 2022. Most identified they currently fall on the lower end of the maturity curve.
Given the elevated threat environment, it’s critical company directors remain engaged and supportive of efforts by information technology and security teams to reduce their risk exposure.
Brett Winterford is Chief Security Officer for Asia Pacific at Okta
The views and opinions expressed in this communication are those of the author and may not necessarily state or reflect those of ANZ.
-
-
-
anzcomau:Bluenotes/technology-innovation,anzcomau:Bluenotes/business-finance
Zero trust in business cyber security
2022-04-01
/content/dam/anzcomau/bluenotes/images/articles/2022/March/AdobeStock_305045172.jpeg
EDITOR'S PICKS
-
Cyber criminals are taking advantage of vulnerabilities caused by the pandemic to attempt to infiltrate businesses more than ever before.
30 June 2021 -
The financial services industry is among the best equipped for disaster after a focus on future investment through the pandemic.
25 June 2021